SOFTWARE SECURITY
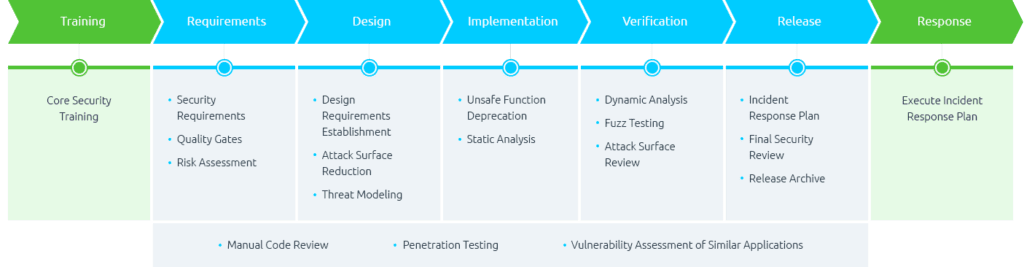
Gain security insights, take action faster and modernize your architecture with DevOps Technologies , we defend against cyberattacks with proactive, focused, industry-relevant threat intelligence to give you the confidence that comes from knowing your business is secure. Anytime. Anywhere.